
Check Point CloudGuard for AWS easily extends comprehensive Threat Prevention security to the AWS cloud and protects assets in the cloud from attacks, and at the same time enables secure connectivity.
Use CloudGuard Network to enforce consistent Security Policies across your entire organization. It protects data between the corporate network and the Amazon VPC. CloudGuard Network inspects data that enters and leaves the private subnet in the Amazon VPC to prevent attacks and mitigate data loss or leakage. CloudGuard Network protects services in the public cloud from the most sophisticated threats, unapproved access, and prevents application layer Denial of Service (DoS) attacks.

Note - For the list of supported versions, refer to the Support Life Cycle Policy.
You are responsible for the cost of the AWS services that you use, when you deploy the solution described in this guide.
The AWS CloudFormation template for the Security VPC includes parameters that you can configure. Some of these settings, such as instance type have an effect on the cost of deployment. For estimated costs, see the AWS pricing calculator.
This Transit VPC - Transit Gateway solution uses Amazon Machine Images (AMIs) from the AWS Marketplace. You must subscribe to Check Point CloudGuard in the AWS Marketplace before you start the deployment.
Check Point CloudGuard Security Gateways , Check Point CloudGuard Security Management Server, and AWS CloudFormation templates described in this guide must have a license. There are two licensing options:
To buy BYOL licenses, contact Check Point Sales
Before you use this solution, make sure you read the AWS terms and services:
If you are new to AWS , see Getting Started with AWS .
Auto Scaling is a service offered by Amazon Web Services ( AWS ) that helps customers automatically adjust their Amazon EC2 capacity based on the current load.
A typical use case consists of a web application served by multiple web servers that are deployed across multiple Availability Zones. An Elastic Load Balancer (ELB) distributes network traffic across this group of web servers.
The Amazon EC2 Auto Scaling service increases or decreases the number of web servers based on the current load.
In the current cyber landscape, it is crucial to protect these environments from attackers. Any security solution used must be as scalable as the setup that it protects.
In addition, it is important that as the number of protected resources scales up or down, so does the number of protecting gateways.
The diagram shows Auto Scaling Group architecture for Check Point CloudGuard Network AWS , an end-to-end solution, which includes:
The Check Point Auto Scaling Group is set up to increase or decrease the number of Check Point Security Gateways in the group based on AWS Cloud Watch metrics.
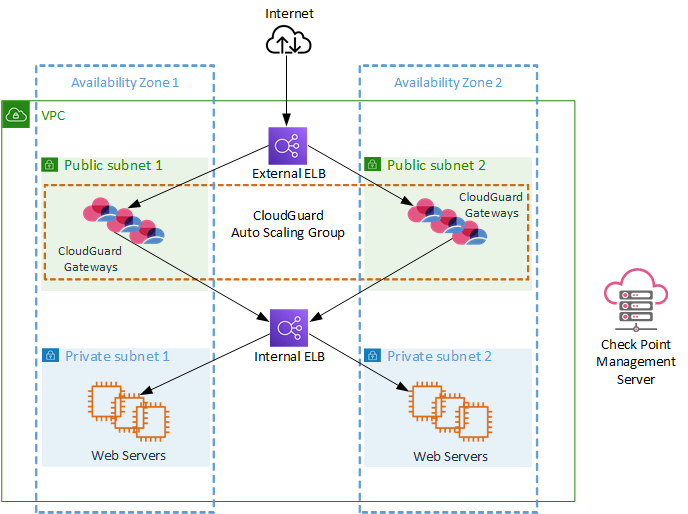

Note - There are few supported types of ELB, before selecting which ELB to deploy, see AWS Elastic Load Balancing.
A Security Policy package is a collection of different types of policies that are enforced after you install the policy on the Security Gateways .
A policy package can have one or more of these policy types:
The Standard policy package is the default Security Policy defined in a newly deployed Security Management Server. Each policy package has a default cleanup rule that drops all traffic.
When you configure Cloud Management Extention (CME) on the Check Point Security Management Server with the autoprov_cfg utility, specify the name of the Security Policy package to be installed on the Auto Scaling group instances with the -po parameter. For the default Security Policy, use the value "Standard" (a capital "S" is required), for this parameter.
If you want to configure more policy packages and install a different policy package on the Security Gateways deployed for the Auto Scaling group solution, then specify the name that you want to give that policy package when you run autoprov_cfg. Afterward, create and configure the policy by connecting to your Security Management Server with SmartConsole.
A scale out event can occur if the current load increases over a preconfigured threshold.
When a scale out event is triggered:
Auto Scaling launches one or more new instances of the Check Point Security Gateway.
The new instances automatically execute the Check Point First Time Configuration Wizard and then reboot.
In the meantime, the CME that is running on the Check Point Management Server detects that new Check Point instances have been launched.
It waits until the gateways have finalized the First Time Configuration Wizard, and then automatically:
Initializes a Secure Internal Communication (SIC) channel with them.
Makes any necessary changes to the Security and Network Address Translation (NAT) policies.
Installs a Security Policy on them.
After a Security Policy is installed on these gateways, the external ELB automatically recognizes the newly created gateways as InService and starts forwarding new connections to them.
The newly created gateways report status and send logs to the Check Point Management Server .
A scale in event can occur as a result of a decrease of the current load below a preconfigured threshold.
When a scale in event is triggered, Auto Scaling designates one or more of the gateways as candidates for termination.
The external ELB stops forwarding new connections to these gateways, and later Auto Scaling terminates them.
The CME that is running on the Check Point Management Server detects that these gateways have been terminated and automatically:
Cleans up any automatically created rules in the Security and Network Address Translation (NAT) policies.
Deletes the gateways from its database.
You should have at least 2 Security Gateways - one in each Availability Zone, for redundancy and availability purposes.